Switch SIEMs without the months-long migration
Move between SIEMs in as little as days, without re-building pipelines, connectors, or schemas. Reduce migration risk, accelerate activation, and keep investigations running throughout the transition.
Show me howWhat a Faster, Safer SIEM Migration Looks Like
Faster activation
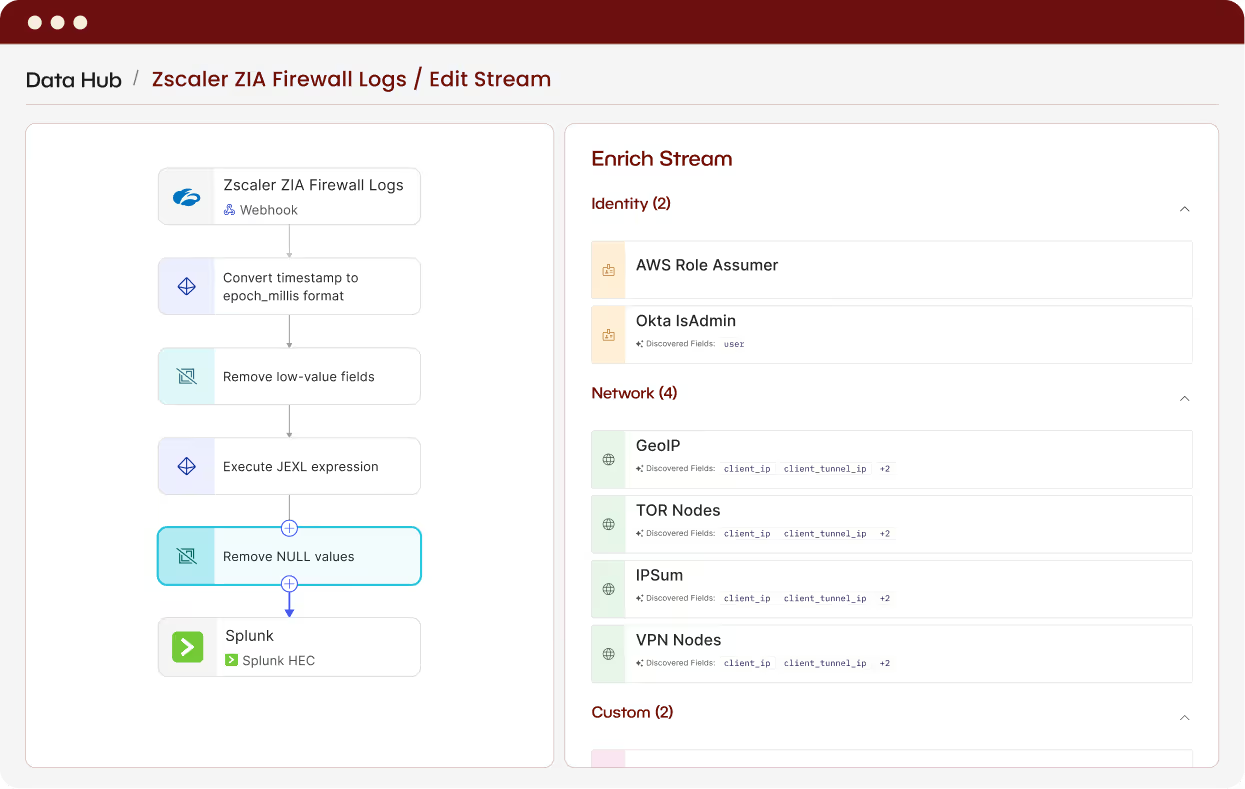
Pre-built security mappings and Recipes normalize data into consistent schemas, so your new SIEM becomes usable immediately.
Zero pipeline rebuild
Beacon handles routing, transformation, and enrichment – eliminating the typical months of engineering required in SIEM migrations.
No downtime
Run the same clean, enriched dataset in both SIEMs during the cutover for uninterrupted detections and investigations.
Capabilities Behind Zero-Downtime Migration
.png)
.png)
Beacon's security-driven data platform optimizes terabytes of important security logs spanning many sources. Data arrives enriched and normalized, and in the case of bloated VPC flow logs, reduced to 5% of their original size, enabling our security team and AI workflows to act immediately and effectively. We no longer choose between coverage and cost efficiency. We now have both, supported by a responsive team of security data experts.
Frequently Asked Questions
Beacon decouples your data sources from your SIEM by acting as a unified collection, normalization, and routing layer. This means you can send the same clean, enriched dataset to both the legacy SIEM and the new SIEM – eliminating the need to rebuild connectors or pipelines.
Teams often reduce migration timelines from months to weeks or even days. Beacon’s pre-built connectors, schema mappings, and Recipes accelerate SIEM activation and reduce the engineering effort required to stand up a new environment.
Yes. Beacon enables dual routing so that both SIEMs receive identical structured data. This makes validation, rule tuning, and side-by-side comparison simple and low risk.
Absolutely. Beacon’s AI-powered normalization translates security data into into ECS, OCSF, UDM or ASIM, ensuring a fast, consistent onboarding experience and minimizing ingest failures.
Beacon provides connector health monitoring, schema validation, automated coverage assessments, and a responsive team of experts. This ensures that no sources break during the cutover, and no data gaps emerge while transitioning platforms, and that timelines are strictly met.
Beacon is built to give teams flexibility and support the collection approach that works best for them. You can continue using your existing agents or collectors, or choose to replace collection infrastructure that’s tightly coupled to your current SIEM. Beacon supports both options, so you can migrate without being forced into unnecessary changes.
Yes. By centralizing collection and normalization, Beacon gives you data portability – making it easy to switch SIEMs again in the future, adopt a multi-SIEM strategy, or send different datasets to different tools.
Definitely. After migration, customers continue to rely on Beacon as their ongoing security data management platform for cost optimization, coverage assurance, enrichment, and agentic SOC enablement.