Cut SIEM costs without losing coverage
Beacon reduces SIEM ingestion dramatically with security-aware optimization – without sacrificing detection fidelity or investigative value. Teams get predictable spend, complete coverage, and cleaner data that accelerates both analysts and AI agents.
Show me howSecurity-First Cost Optimization, Not Blind Reduction
Slash ingest volume
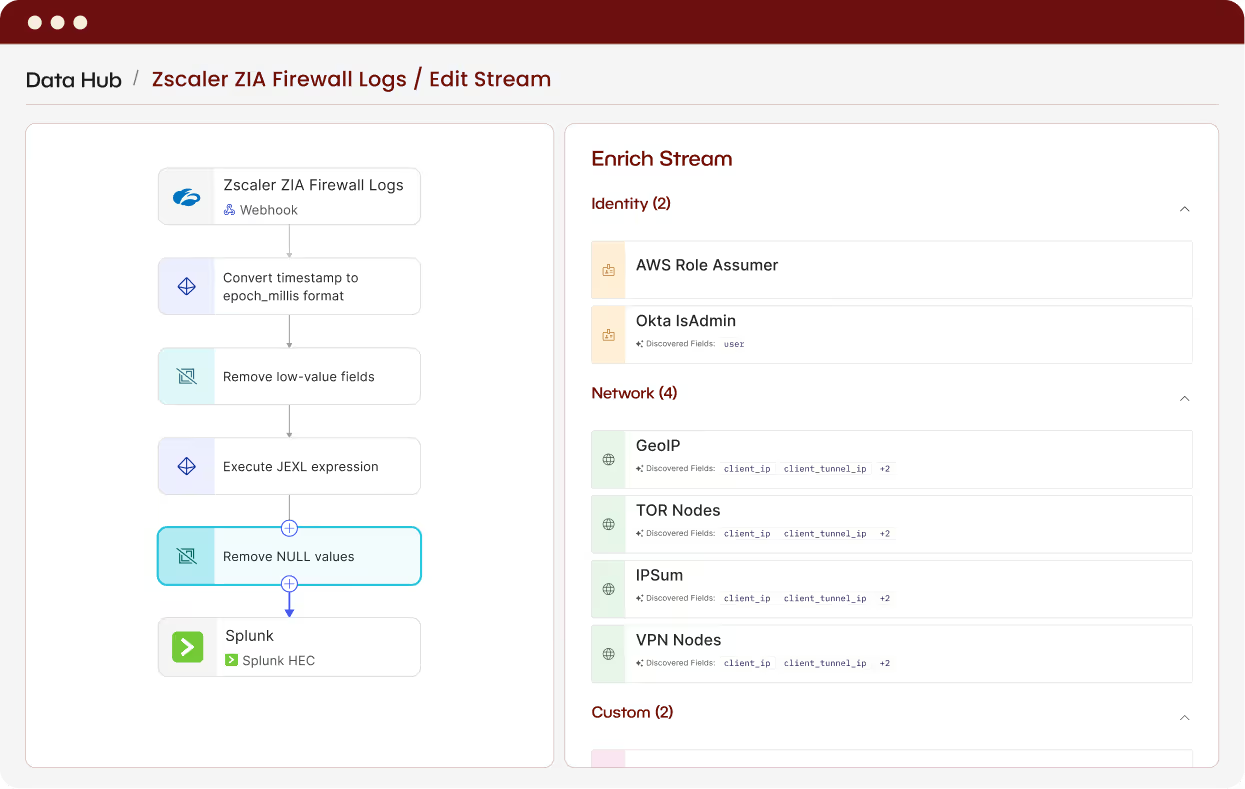
Beacon’s security-driven Recipes filter redundant and low-value telemetry while preserving the information required for detection and investigation.
Preserve detection fidelity
Unlike generic ETL tools, Beacon optimizes with attacker-aware logic so teams cut cost while maintaining full detection coverage.
Make spend predictable
Decouple your data strategy from SIEM pricing – route logs intelligently across cold storage, data lakes, and SIEM to keep budgets stable.
Inside Beacon's Security-Aware Optimization Engine
.png)
.png)
.png)
Beacon's security-driven data platform optimizes terabytes of important security logs spanning many sources. Data arrives enriched and normalized, and in the case of bloated VPC flow logs, reduced to 5% of their original size, enabling our security team and AI workflows to act immediately and effectively. We no longer choose between coverage and cost efficiency. We now have both, supported by a responsive team of security data experts.
Frequently Asked Questions
Beacon uses security-aware optimization Recipes, built by practitioners and validated against real attack patterns, to filter redundant or low-value telemetry while preserving the exact fields required for detections and investigations. This allows teams to safely cut SIEM ingest volume by 60–98% while maintaining or improving detection quality.
No. Beacon optimizes logs before they reach the SIEM but does not remove fields that detection rules, correlation logic, or investigations depend on. Analysts and AI agents continue operating on complete, normalized, and enriched data – often with better context than before.
Beacon delivers the highest savings on high-volume telemetry such as VPC Flow Logs, Cloudflare, WAF, firewall logs, EDR telemetry, SaaS audit logs, and more. Many of these sources see 70–98% volume reduction without loss of security value.
Yes. Beacon supports smart routing that sends high-value logs to your SIEM while directing archival or compliance logs to cold storage or data lakes. This reduces both ongoing ingestion fees and long-term retention costs.
Most teams see measurable SIEM cost reduction within hours or days, not months. Beacon’s pre-built, production-ready Recipes remove the need for long tuning cycles or custom engineering work.
No. Beacon works with all major SIEMs, enhancing and optimizing the data you already send today. It helps you reduce cost and improve detection quality – without migrating away from your current SIEM.
Yes. Generic ETL and log routing tools lack the domain-specific logic needed for safe security log optimization. Beacon can operate alongside or replace those tools, providing security-first reduction, enrichment, normalization, and pipeline health monitoring.
Native filters often remove data blindly and do not understand attacker behavior, schema requirements, or cross-source correlations. Beacon takes a security-driven, context-aware approach that preserves fidelity while achieving far greater reduction rates safely.