The data layer for modern security operations
Seamlessly collect, reduce, enrich, and route your security data — so analysts and AI agents have the context they need to detect and stop threats faster.
Show me howSecurity teams face an impossible tradeoff: coverage, context, cost
More telemetry was supposed to make you safer. Instead, it made everything harder.
Data overload and blind spots
Security teams are drowning in telemetry. There’s too much to store, too much to analyze – and the result is missed threats hiding in the noise.
Endless engineering upkeep
Instead of threat hunting, your best people are fixing pipelines. Fragile integrations and brittle enrichment logic sap security time and talent.
Soaring costs, shrinking visibility
Every extra log blows up your SIEM bill. So you cut coverage to save money — and lose context right when you need it most.
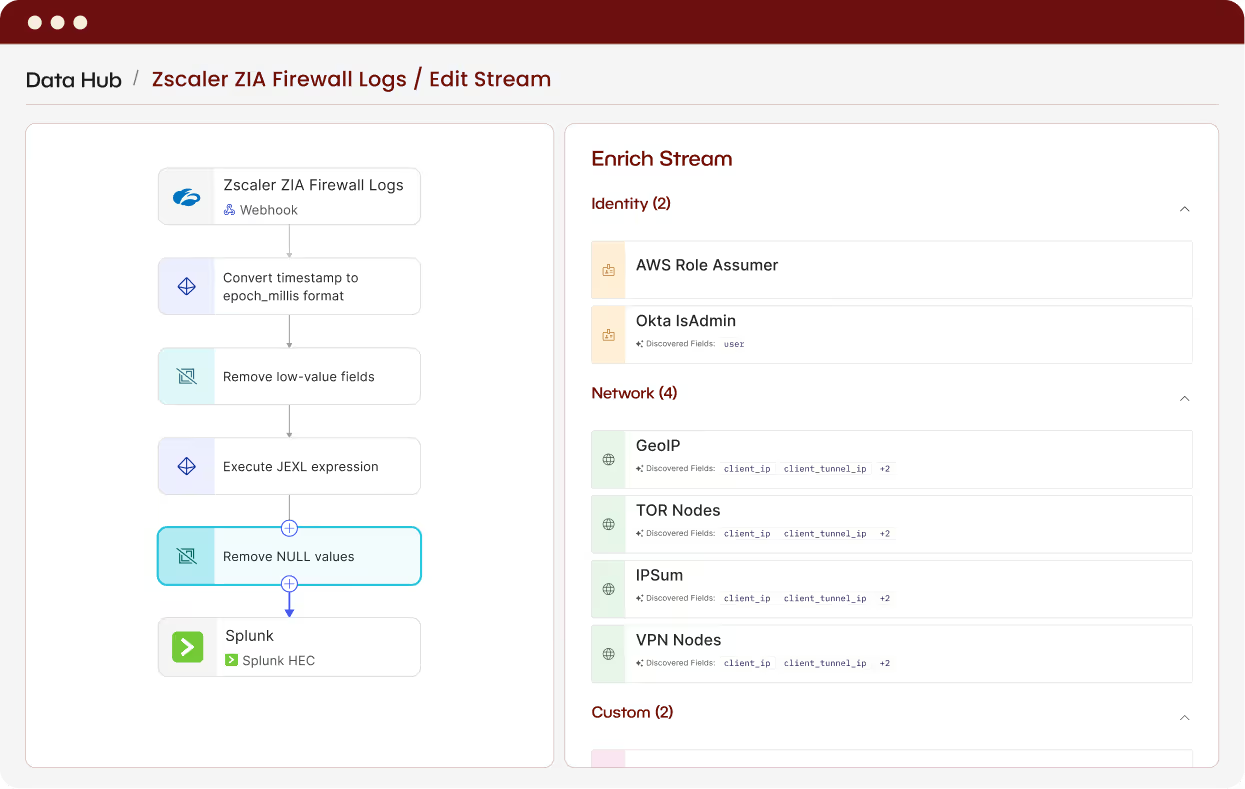
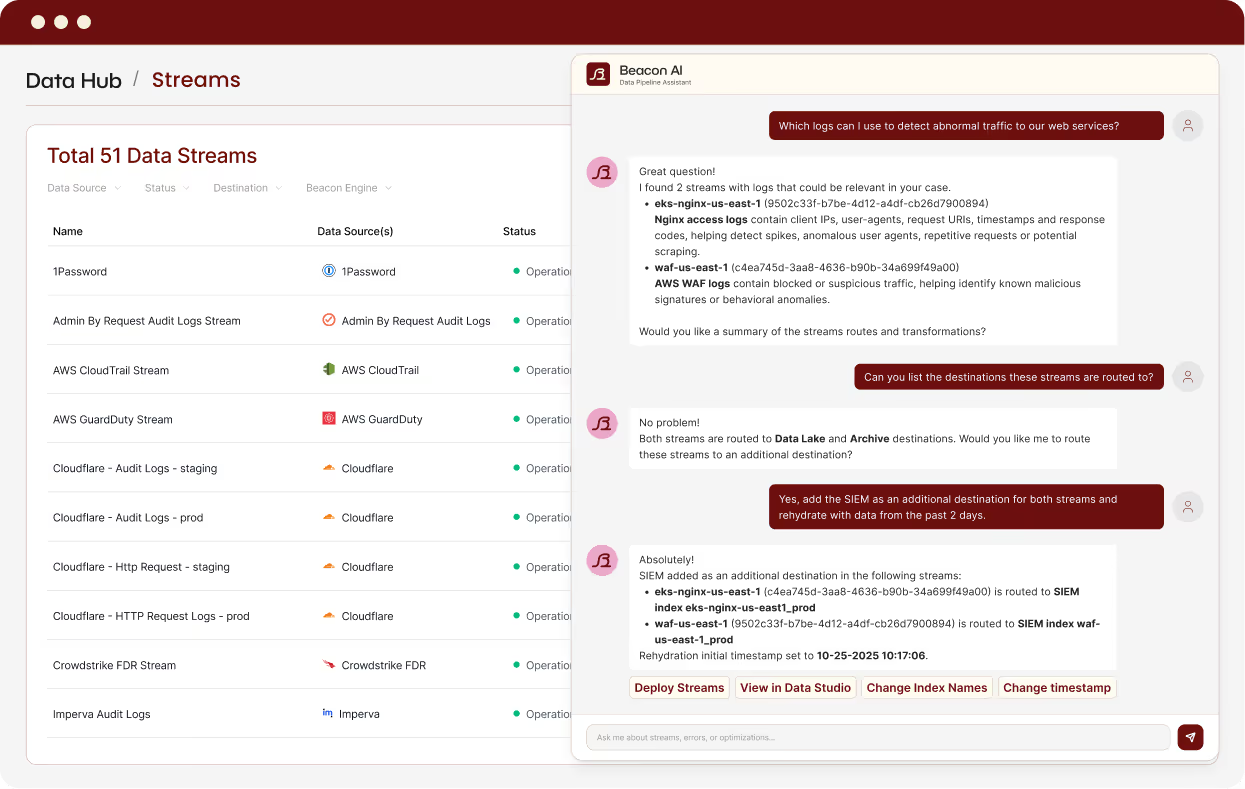
Beacon helps you harness your data for better, faster security
Investigate faster – no data-wrangling required
Beacon delivers clean, context-rich telemetry your analysts and AI agents can actually use. No more data engineering tax, just faster answers and fewer blind spots.
See what's missing before attackers do
Automatically map your environment, surface missing sources, and connect what’s broken. Coverage gaps close themselves before they become problems.
Reduce costs without losing coverage
Keep the signal, drop the noise. Optimization recipes — built on real attack data and vetted by security researchers — preserve what actually matters for detection and investigation.
Beacon


.png)
.png)
.png)
.png)
Beacon's security-driven data platform optimizes terabytes of important security logs spanning many sources. Data arrives enriched and normalized, and in the case of bloated VPC flow logs, reduced to 5% of their original size, enabling our security team and AI workflows to act immediately and effectively. We no longer choose between coverage and cost efficiency. We now have both, supported by a responsive team of security data experts.
Why Security Teams Choose Beacon
Built by security practitioners
(not ETL engineers)
Our team includes incident responders, threat researchers, and offensive security experts. Every recipe is tested against real attack patterns, not theoretical optimization.
Pre-built recipes and workflows, zero consultants required
Deploy production pipelines in minutes with ready-to-use optimization logic, enrichment strategies, and connectors. No six-month implementation projects or professional services teams.
Enterprise-grade from day one
SOC 2 Type II and ISO 27001 compliant with multi-cloud, multi-region, and bring-your-own-cloud deployment options that meet your data residency and sovereignty requirements.
Beacon doesn’t just move logs around; it tells you which logs matter and how to use them.
security-optimized.