Security-first data pipeline for Google SecOps
Ingest and route security data from any source into Google SecOps with security-aware optimization, enrichment, and high-fidelity UDM normalization – improving detection and investigation coverage with less operational overhead.
Show me howNormalized, investigation-ready data in Google SecOps in minutes
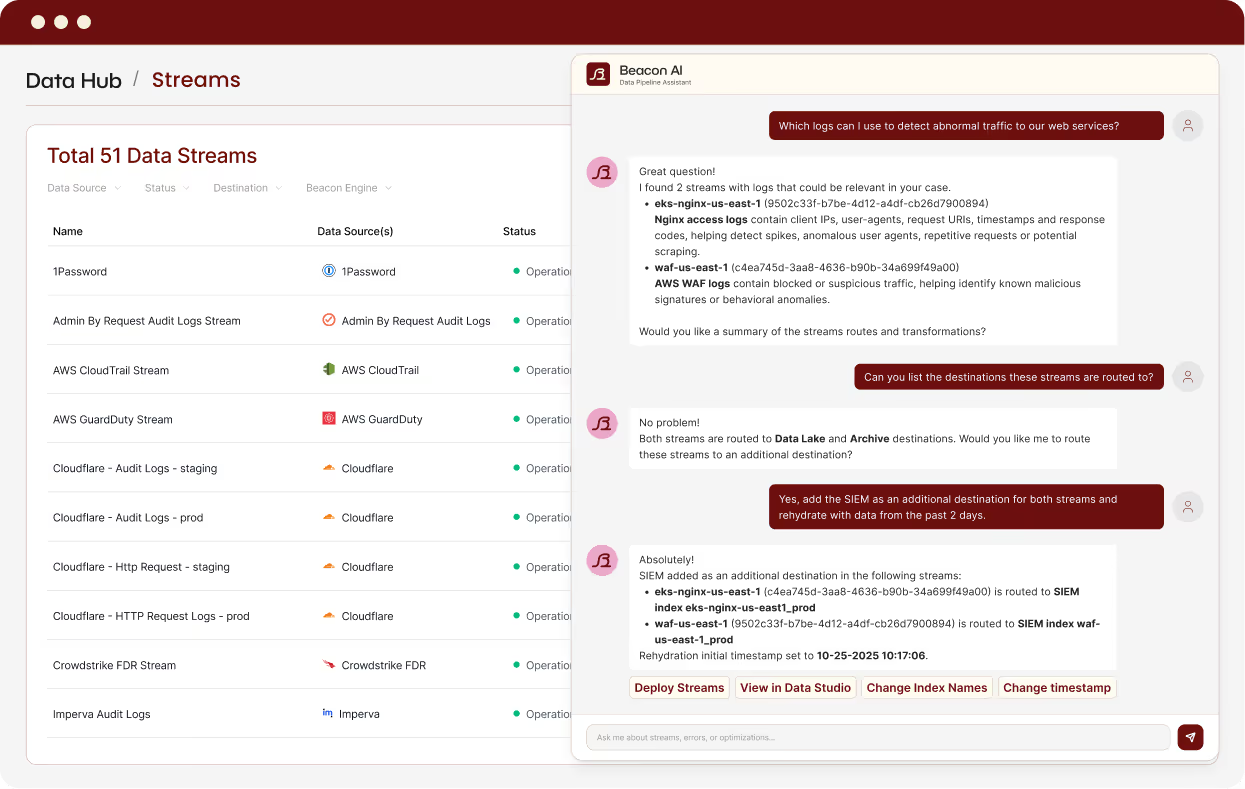
Expand coverage with any data source
Ingest security data from sources Google SecOps doesn't natively support and normalize them to UDM. Get consistent detections across your entire environment, not just the logs Google already handles.
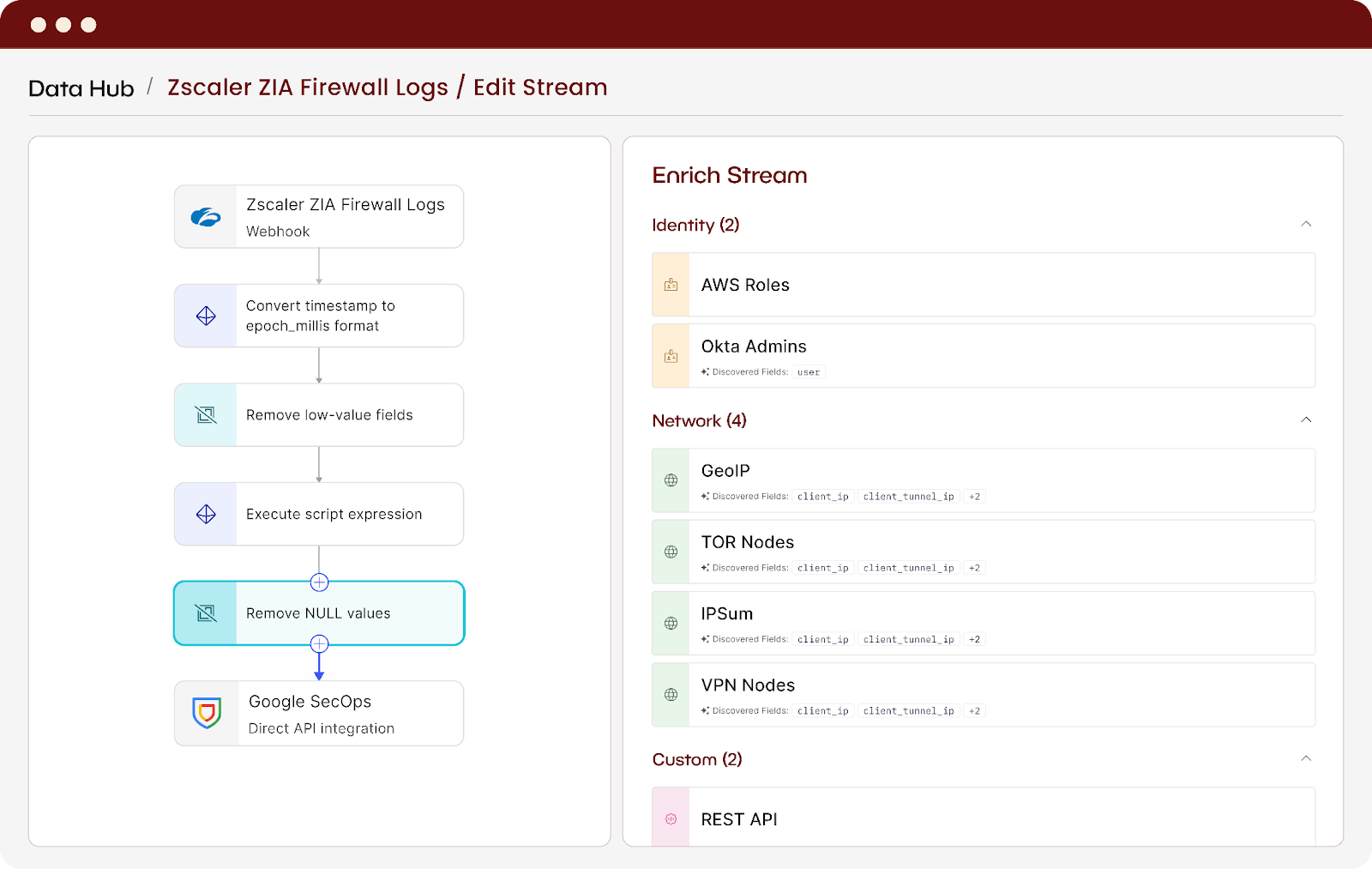
Fewer pipelines, less ongoing work
Out-of-the-box UDM mappings, transformations, and integrations eliminate the need to build and maintain custom parsers. Start routing normalized data to Google SecOps in minutes, not months.
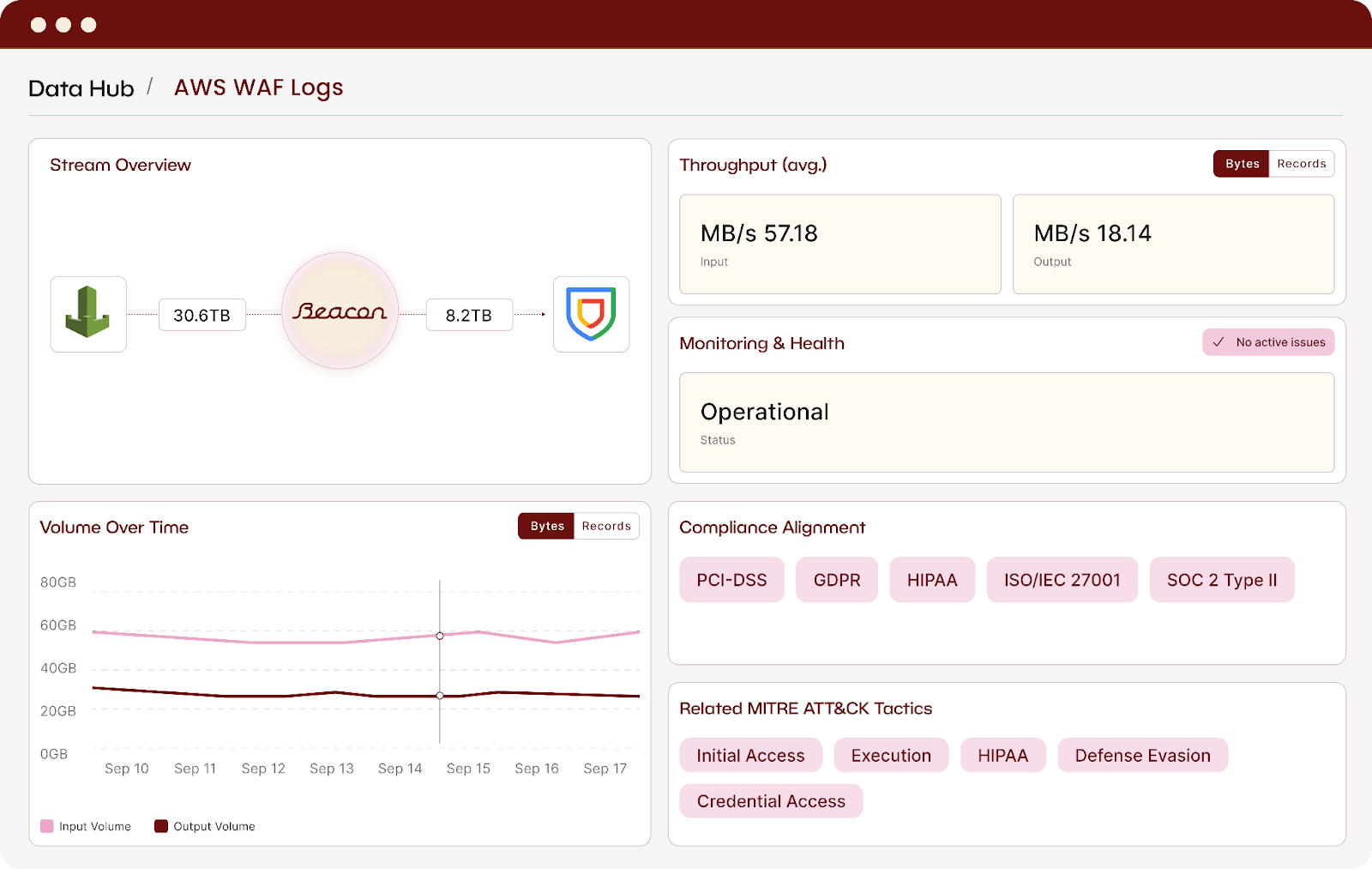
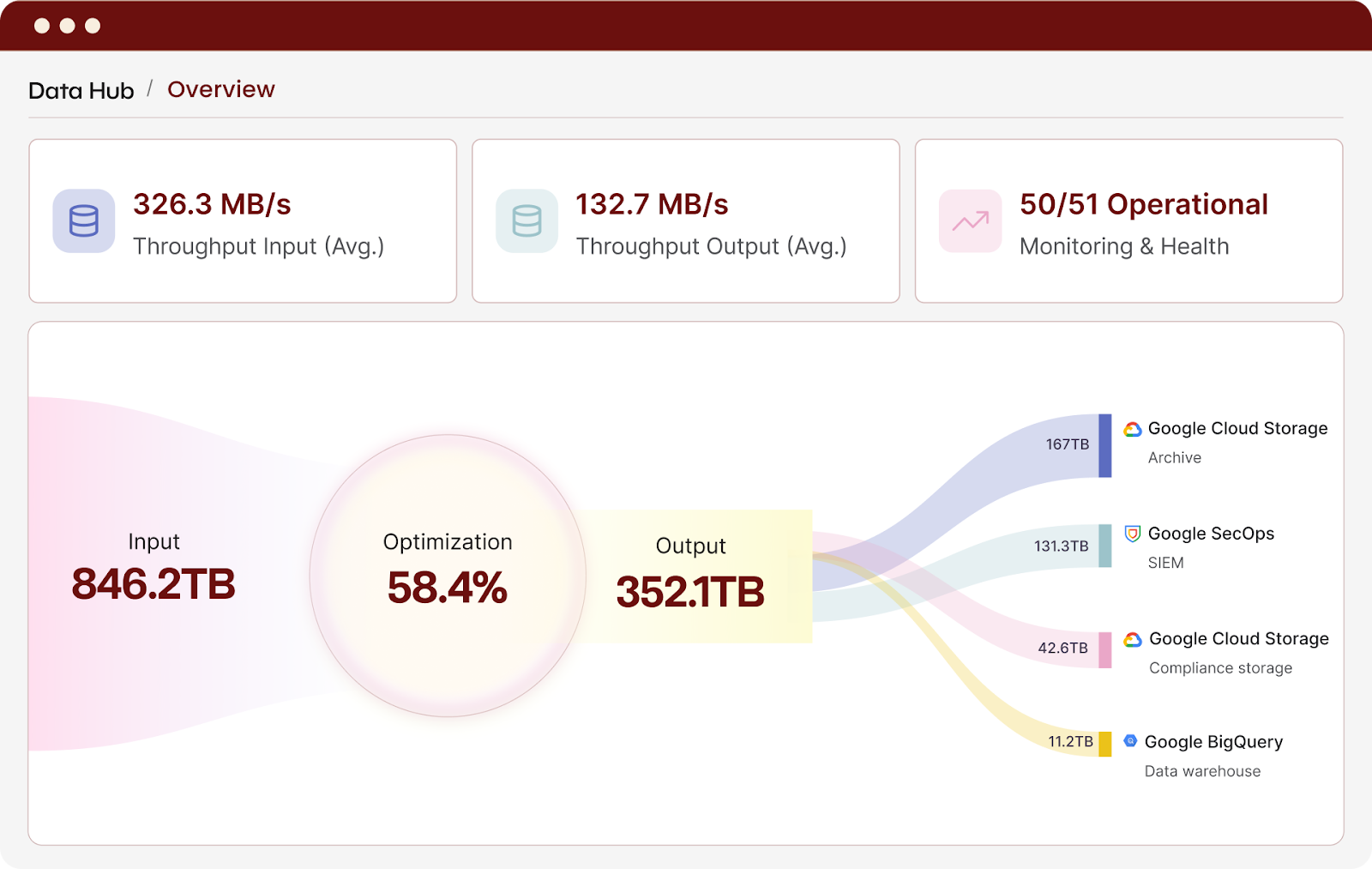
Security-aware optimization and enrichment
Beacon reduces volume with security-aware logic and adds critical context before data reaches Google SecOps. This improves detection and investigation fidelity while lowering operational cost.
Power Google SecOps with richer, more complete data

.png)
.png)
.png)
Beacon's security-driven data platform optimizes terabytes of important security logs spanning many sources. Data arrives enriched and normalized, and in the case of bloated VPC flow logs, reduced to 5% of their original size, enabling our security team and AI workflows to act immediately and effectively. We no longer choose between coverage and cost efficiency. We now have both, supported by a responsive team of security data experts.
Why Security Teams Choose Beacon
Built by security practitioners
(not ETL engineers)
Our team includes incident responders, threat researchers, and offensive security experts. Every recipe is tested against real attack patterns, not theoretical optimization.
Pre-built recipes and workflows, zero consultants required
Deploy production pipelines in minutes with ready-to-use optimization logic, enrichment strategies, and connectors. No six-month implementation projects or professional services teams.
Enterprise-grade from day one
SOC 2 Type II and ISO 27001 compliant with multi-cloud, multi-region, and bring-your-own-cloud deployment options that meet your data residency and sovereignty requirements.
Beacon doesn’t just move logs around; it tells you which logs matter and how to use them.
security-optimized.






